Lambda Block TCP Connection
Lambda Block TCP Connection is an AWS fault that simulates network blocks for TCP connections of a Lambda function. This fault helps you evaluate how your application responds when outbound TCP connections from a Lambda function are blocked.
Use cases
- Simulate network blocks to test Lambda function resilience.
- Evaluate the impact of blocked TCP connections on application performance and error handling.
- Test fallback mechanisms and error reporting in serverless architectures.
Prerequisites
- Kubernetes >= 1.17
- The Lambda function must be up and running.
- Kubernetes secret must have the AWS access configuration (key) in the
CHAOS_NAMESPACE. Below is a sample secret file:apiVersion: v1
kind: Secret
metadata:
name: cloud-secret
type: Opaque
stringData:
cloud_config.yml: |-
# Add the cloud AWS credentials respectively
[default]
aws_access_key_id = XXXXXXXXXXXXXXXXXXX
aws_secret_access_key = XXXXXXXXXXXXXXX
HCE recommends that you use the same secret name, that is, cloud-secret. Otherwise, you will need to update the AWS_SHARED_CREDENTIALS_FILE environment variable in the fault template with the new secret name and you won't be able to use the default health check probes.
Below is an example AWS policy to execute the fault.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"lambda:GetFunction",
"lambda:GetFunctionConfiguration",
"lambda:UpdateFunctionConfiguration"
],
"Resource": "*"
}
]
}
- Go to superset permission/policy to execute all AWS faults.
- Go to the common tunables and AWS-specific tunables to tune the common tunables for all faults and AWS-specific tunables.
- Go to AWS named profile for chaos to use a different profile for AWS faults.
- Currently, it is supported in Python; support for other languages is coming soon.
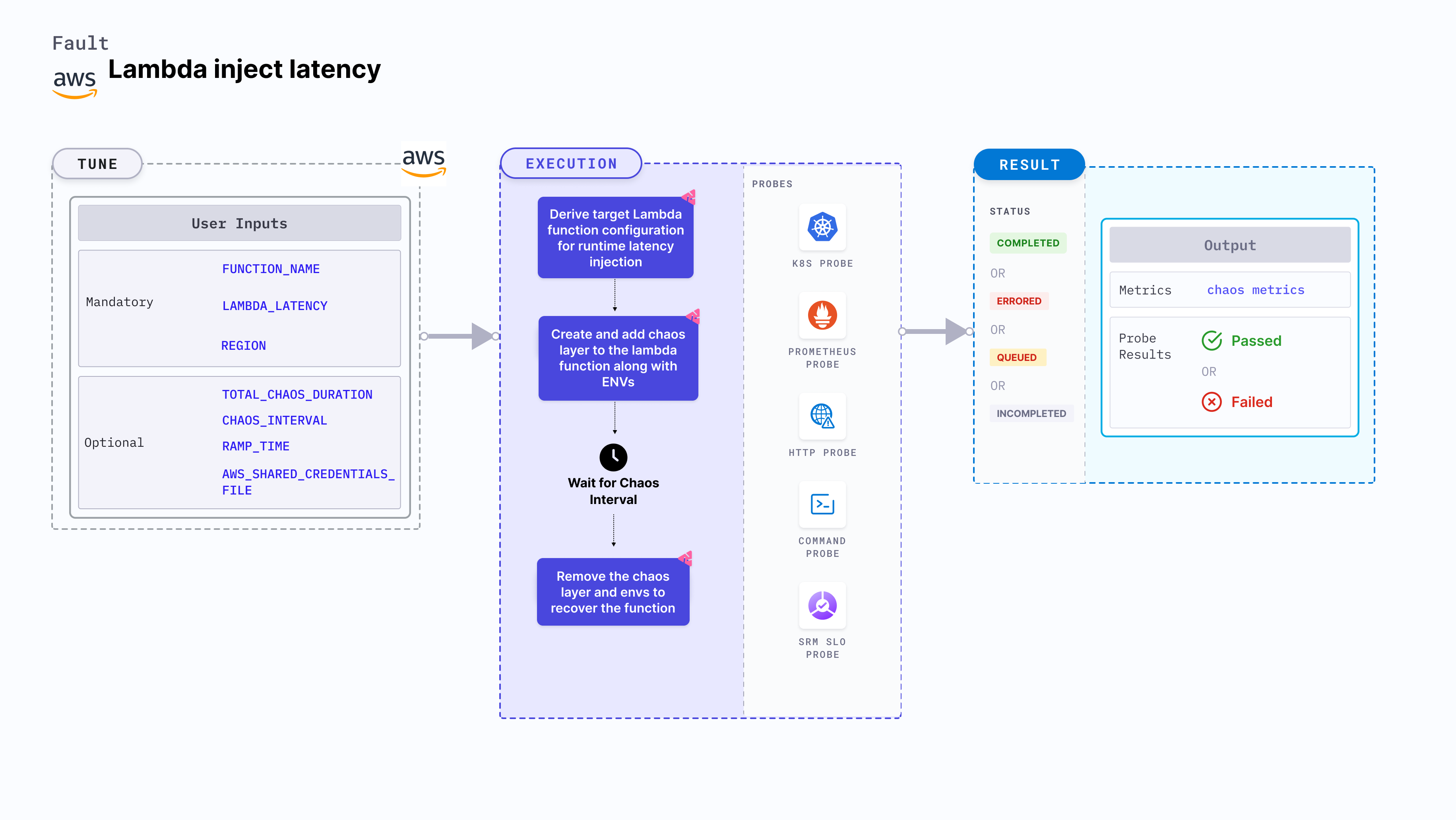
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| FUNCTION_NAME | Name of the target Lambda function. | For example, test-function. For more information, go to function name. |
| REGION | The AWS region where the Lambda function is deployed. | For example, us-east-1. For more information, go to region. |
| TARGET_HOSTNAMES | Comma-separated list of hostnames to block TCP connections to. | For example, example.com,api.example.com. For more information, go to target hostnames. |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | Duration for which chaos is injected (in seconds). | Default: 30 s. For more information, go to duration of the chaos. |
| CHAOS_INTERVAL | The interval (in seconds) between successive network block attempts. | Default: 30 s. For more information, go to chaos interval. |
| AWS_SHARED_CREDENTIALS_FILE | Path to the AWS secret credentials. | Default: /tmp/cloud_config.yml. For more information, go to AWS shared credentials file. |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | Optional. For more information, go to ramp time. |
Target Hostnames
The TARGET_HOSTNAMES environment variable defines the list of hostnames to which TCP connections should be blocked from the target Lambda function during chaos execution.
Block TCP connections to specific hostnames from a Lambda function.
---
# Block TCP connections to specific hostnames from a Lambda function
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: lambda-block-tcp-connection
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: lambda-block-tcp-connection
spec:
components:
env:
- name: TARGET_HOSTNAMES
value: 'example.com,api.example.com'
Function Name
The FUNCTION_NAME environment variable specifies the name of the target AWS Lambda function whose host will be subjected to chaos.
---
# Block TCP connections from a specific Lambda function
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: lambda-block-tcp-connection
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: lambda-block-tcp-connection
spec:
components:
env:
- name: FUNCTION_NAME
value: 'test-function'